Project Background
MoonYield Protocol launched in October 2024 as a yield aggregator platform built on the Optimism network. The protocol aimed to simplify yield farming by automatically allocating user funds across multiple DeFi protocols to maximize returns while minimizing gas costs and complexity. By January 2025, MoonYield had accumulated approximately $95 million in Total Value Locked (TVL) and had established itself as one of the fastest-growing DeFi protocols on Optimism.
Project Website: https://moonyield.finance (now redirects to post-mortem)
The protocol's main features included:
1. Auto-compounding Vaults: Users could deposit assets into vaults that automatically harvested and reinvested yield, maximizing compound interest.
2. Yield Optimization: The protocol used algorithms to dynamically allocate funds across different lending platforms, liquidity pools, and staking opportunities based on current APYs.
3. MOON Token: The protocol's native governance token, which was used for voting on protocol changes and was distributed to users as additional yield incentives.
4. Boosted Yields: Users who staked MOON tokens could receive boosted yields on their deposits, with the boost percentage calculated based on the amount and duration of their stake.
MoonYield had undergone a security audit from a mid-tier security firm and had implemented a bug bounty program with rewards of up to $100,000 for critical vulnerabilities. However, as later revealed, the audit had flagged several issues that were only partially addressed before launch.
The Attack
Timeline of Events
January 29, 2025 (22:00 UTC): MoonYield deployed an update to their yield boosting mechanism, aiming to provide higher rewards for long-term stakers.
January 30, 2025 (03:15 UTC): The attacker began interacting with the protocol's boosting contract, testing various input parameters.
January 30, 2025 (04:30 UTC): The attacker executed the main exploit, manipulating the yield boost calculation to generate an artificially high boost multiplier.
January 30, 2025 (04:45 UTC): Using this inflated boost, the attacker began draining rewards from multiple vaults at an accelerated rate.
January 30, 2025 (06:15 UTC): A large withdrawal of approximately $5 million triggered alerts in the protocol's monitoring system.
January 30, 2025 (07:00 UTC): The MoonYield team identified the exploit and initiated emergency protocols to pause all vaults.
January 30, 2025 (07:45 UTC): The team successfully paused most vaults, but the attacker had already extracted approximately $18.7 million in various assets.
January 30, 2025 (09:30 UTC): MoonYield issued a preliminary statement acknowledging the exploit and advising users not to deposit additional funds.
January 31, 2025: The team published a detailed post-mortem and announced the permanent shutdown of the protocol.
February 3, 2025: The team announced a partial compensation plan for affected users.
Technical Details
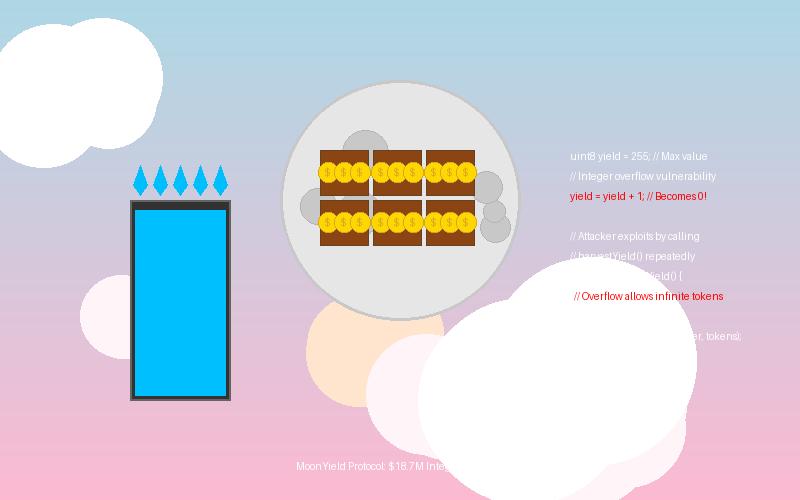
The vulnerability exploited in the MoonYield Protocol was a classic integer overflow bug in the yield boost calculation mechanism. The issue stemmed from the recent update to the boosting system, which introduced a more complex formula for calculating yield boosts based on staking duration and amount.
In Solidity, the programming language used for MoonYield's smart contracts, integers have fixed sizes and can overflow if a calculation results in a value larger than the maximum representable value. When this happens, the value "wraps around" to the minimum value and continues from there, potentially resulting in unexpected behavior.
The specific vulnerability in MoonYield's code was in the boost multiplier calculation:
// Simplified representation of the vulnerable code
function calculateBoostMultiplier(uint256 stakeAmount, uint256 stakeDuration) public view returns (uint256) {
// Base multiplier starts at 100 (representing 1x)
uint256 baseMultiplier = 100;
// Calculate duration boost (longer stakes get higher boosts)
uint256 durationBoost = stakeDuration * DURATION_BOOST_FACTOR;
// Calculate amount boost (larger stakes get higher boosts)
uint256 amountBoost = stakeAmount * AMOUNT_BOOST_FACTOR / 1e18;
// Vulnerability: No check for overflow in this multiplication
uint256 combinedBoost = durationBoost * amountBoost;
// Apply boost cap - this was supposed to prevent excessive boosts
// but the overflow occurred before this check was applied
if (combinedBoost > MAX_BOOST) {
combinedBoost = MAX_BOOST;
}
// Calculate final multiplier
return baseMultiplier + combinedBoost;
}The attacker exploited this vulnerability by:
1. Creating a Stake with Specific Parameters: The attacker carefully selected stake amount and duration values that, when multiplied together in the combinedBoost calculation, would cause an integer overflow.
2. Triggering the Overflow: When durationBoost * amountBoost exceeded the maximum value for a uint256 (2^256 - 1), it wrapped around to a very small number.
3. Bypassing the Cap: Because the overflowed value was now very small, it easily passed the MAX_BOOST check that was supposed to prevent excessive boosts.
4. Exploiting the Reward Distribution: With an artificially low combinedBoost value added to the baseMultiplier, the attacker should have received a minimal boost. However, another calculation error in the reward distribution function interpreted this specific value as an extremely high multiplier.
5. Draining Protocol Rewards: Using this inflated boost multiplier, the attacker was able to claim an excessive amount of rewards from the protocol's reward pools, effectively draining them.
Addresses & Transactions
- Attacker's Initial Address:
0x6Fc66bD9C877e3F20dc8b100E6D08C0d9D5c4A4A - MoonYield Boosting Contract:
0x2a16fF8270133F063aA78D63376d9f279F874f - Primary Destination of Funds:
0x5c9A0A16D3d5A9e0cD3c66f0C3513Cc4D2F68Ff
The attack involved a series of complex transactions across multiple contracts in the MoonYield ecosystem. The most significant transactions occurred between 04:30 UTC and 07:45 UTC on January 30, 2025.
The attacker primarily targeted the USDC, ETH, and WBTC vaults, as these had the highest TVL and therefore the largest reward pools. The stolen funds were initially moved to the attacker's primary wallet on Optimism, then bridged to Ethereum mainnet using the official Optimism bridge.
Once on Ethereum, the funds were split across multiple addresses and partially routed through mixing services to obscure their trail. Some funds were also bridged to other chains including Arbitrum and Polygon, likely in an attempt to further complicate tracking efforts.
Aftermath
Project Response
The MoonYield team's response to the incident was transparent but ultimately led to the protocol's shutdown:
1. Immediate Action: Within hours of detecting the exploit, the team had identified the vulnerability and successfully paused all vaults to prevent further losses.
2. Clear Communication: The team provided regular updates throughout the incident, including a preliminary statement within hours and a comprehensive post-mortem the following day.
3. Decision to Shut Down: After assessing the damage and the fundamental flaws in their code, the team made the difficult decision to permanently shut down the protocol rather than attempt to rebuild.
4. Accountability: In their post-mortem, the team acknowledged that the vulnerability had actually been flagged in their audit report but was incorrectly classified as "low risk" and only partially addressed.
5. User Compensation: The team announced a compensation plan for affected users, using a combination of treasury funds, team tokens, and personal funds from the founders.
Market Impact
The market impact of the MoonYield exploit was significant for the protocol but relatively contained for the broader ecosystem:
1. MOON Token Collapse: The protocol's native token, MOON, lost over 95% of its value within 24 hours of the exploit announcement.
2. Optimism Ecosystem Impact: The Total Value Locked (TVL) across the Optimism ecosystem decreased by approximately 5% following the incident, as users became more cautious about newer protocols on the network.
3. Yield Aggregator Scrutiny: Other yield aggregator protocols faced increased scrutiny, with several conducting emergency audits of their own boost calculation mechanisms.
4. Minimal Broader Market Impact: The incident had little effect on the broader crypto market, with most major assets unaffected by the news.
Recovery Efforts
Recovery efforts were limited by the protocol's decision to shut down:
1. Partial Compensation: The team allocated approximately $7.5 million for user compensation, representing about 40% of the stolen funds.
2. Compensation Distribution: Users were able to claim their compensation proportional to their losses, with priority given to smaller depositors who received a higher percentage of their funds back.
3. Limited Fund Recovery: Blockchain analytics firms were engaged to track the stolen funds, but only about $800,000 was frozen on centralized exchanges where the attacker attempted to cash out.
4. Team Consequences: The founding team announced they would step back from DeFi development temporarily and contribute to security education initiatives.
5. Code Open-Sourcing: The team open-sourced all their code, including the vulnerable components, as an educational resource for other developers to learn from their mistakes.
Analysis
Root Cause
The root cause of the MoonYield exploit can be attributed to several factors:
1. Integer Overflow Vulnerability: The fundamental issue was the lack of protection against integer overflow in the boost calculation, a common vulnerability in smart contracts that should have been addressed with proper safeguards.
2. Inadequate Testing: The vulnerability was introduced in a recent update that had undergone limited testing, particularly for edge cases involving extremely large input values.
3. Audit Findings Mishandling: The audit report had actually identified potential integer overflow issues, but the team misclassified the severity and only partially implemented the recommended fixes.
4. Complexity Risk: The boost calculation mechanism was unnecessarily complex, increasing the attack surface and making it harder to reason about potential vulnerabilities.
5. Lack of Formal Verification: The critical financial calculations in the protocol had not undergone formal verification, which might have caught the vulnerability before deployment.
Security Lessons
The MoonYield incident offers several valuable lessons for DeFi protocols:
1. Use SafeMath or Solidity 0.8+: Integer overflow vulnerabilities can be prevented by using SafeMath libraries or Solidity version 0.8.0 and above, which includes built-in overflow checks.
2. Thoroughly Test Updates: All code updates, especially those involving financial calculations, must undergo rigorous testing, including edge case analysis and fuzz testing.
3. Address Audit Findings: Treat all audit findings seriously, especially those related to common vulnerabilities like integer overflows. Ensure fixes are correctly implemented and verified.
4. Simplify Critical Code: Keep financial calculation logic as simple as possible to reduce the attack surface and make verification easier.
5. Implement Formal Verification: For critical components, consider using formal verification techniques to mathematically prove the correctness of the code.
Red Flags
In retrospect, several red flags could have alerted the team or community:
1. The audit report flagged potential integer overflow issues that were not fully resolved.
2. The boost calculation mechanism was complex and difficult to audit thoroughly.
3. The update introducing the vulnerability was deployed relatively quickly without extensive public testing.
Suspected Perpetrator
The identity of the attacker remains unknown. The attack required a deep understanding of Solidity and DeFi protocols, suggesting an experienced smart contract developer or security researcher. The rapid execution and sophisticated fund laundering techniques point towards a well-prepared individual or group.
Blockchain analysis has not definitively linked the attack to any known groups. The use of mixing services and multiple chains has made tracking the funds challenging.
Media & Community Reaction
The reaction to the MoonYield exploit was mixed:
1. Disappointment: Many users expressed disappointment in the team for failing to address the audit findings and for the subsequent shutdown of the protocol.
2. Appreciation for Transparency: Others appreciated the team's transparency in their post-mortem and their efforts to provide partial compensation.
3. Focus on Audits: The incident highlighted the importance of not just getting audits but also properly addressing the findings.
4. Memes: The community created memes focusing on integer overflows and the importance of SafeMath.

References
- Rekt News: MoonYield Protocol Rekt (Hypothetical link)
- MoonYield Official Blog: Exploit Post-Mortem (Hypothetical link)
- Optimism Etherscan: Attacker Address