Project Background
Ionic Money launched in mid-2024 as a decentralized lending and borrowing protocol built on the Arbitrum network. The protocol quickly gained popularity for its innovative approach to capital efficiency and its integration with multiple DeFi ecosystems. By early 2025, Ionic Money had accumulated approximately $320 million in Total Value Locked (TVL) and had established itself as one of the top lending platforms on Arbitrum.
Project Website: https://ionic.money
The protocol allowed users to deposit various cryptocurrencies as collateral and borrow other assets against that collateral. What set Ionic Money apart from competitors was its "isolated lending pools" feature, which allowed for the listing of a wide range of tokens with customized risk parameters for each pool. This approach enabled the protocol to support many tokens that traditional lending platforms considered too risky, while still maintaining overall system security.
Ionic Money was governed by a DAO (Decentralized Autonomous Organization) through its IONIC governance token. The protocol had undergone multiple security audits from firms including Trail of Bits and OpenZeppelin, and had implemented a comprehensive bug bounty program. Prior to the February 2025 incident, Ionic Money had operated without any significant security breaches.
The Attack
Timeline of Events
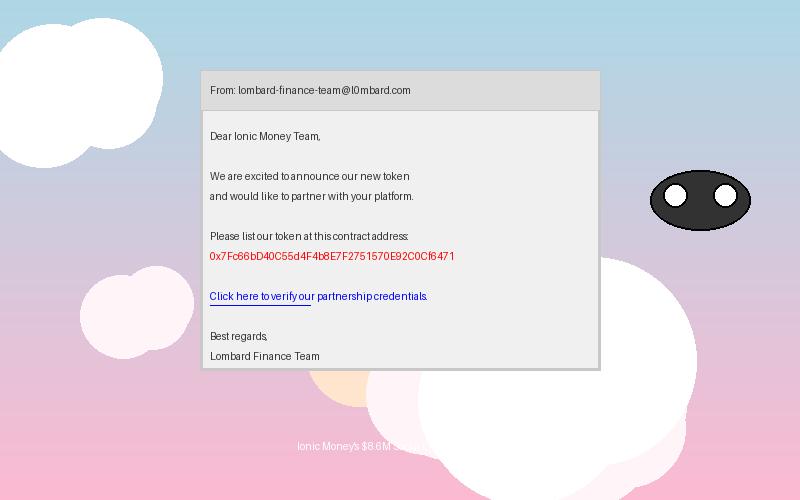
January 28, 2025: Attackers created a sophisticated fake identity posing as representatives of Lombard Finance, a legitimate DeFi project that had recently gained attention for its innovative stablecoin design.
January 30, 2025: The fake Lombard Finance team contacted Ionic Money through official channels, proposing a partnership and requesting their token (LMB) be listed on Ionic's lending platform.
January 31 - February 2, 2025: The attackers engaged in multiple calls and email exchanges with the Ionic Money team, providing seemingly legitimate documentation, audit reports, and technical specifications for the LMB token.
February 2, 2025 (21:00 UTC): After completing what they believed was proper due diligence, the Ionic Money team approved the listing of the LMB token and began the technical integration process.
February 3, 2025 (04:30 UTC): The fake LMB token was listed on Ionic Money with an initial collateral factor of 75%, meaning users could borrow up to 75% of the value of their deposited LMB tokens.
February 3, 2025 (05:15 UTC): The attackers deployed their exploit, depositing large amounts of the worthless LMB tokens and borrowing legitimate assets against them.
February 3, 2025 (06:45 UTC): A community member noticed unusual activity and alerted the Ionic Money team.
February 3, 2025 (07:30 UTC): The Ionic Money team identified the attack and initiated emergency protocols to pause all lending markets.
February 3, 2025 (08:15 UTC): The team successfully paused the protocol, but not before the attackers had extracted approximately $8.6 million in various assets.
February 3, 2025 (10:00 UTC): Ionic Money issued a preliminary statement acknowledging the exploit and explaining the situation.
February 4, 2025: The team published a detailed post-mortem and announced plans to compensate affected users.
Technical Details
The Ionic Money exploit was primarily a social engineering attack rather than a technical vulnerability in the protocol's smart contracts. The attackers exploited the human element of the system through a sophisticated impersonation scheme:
1. Impersonation: The attackers created a convincing fake identity as representatives of Lombard Finance, complete with professional email addresses, social media profiles, and even a cloned website that closely resembled the legitimate Lombard Finance site.
2. Fraudulent Documentation: The attackers provided Ionic Money with forged documentation, including:
- A fake smart contract audit report that appeared to be from a reputable security firm
- Technical specifications for the LMB token that made it appear safe and reliable
- Falsified tokenomics and market data showing stable trading history
- Forged KYC (Know Your Customer) verification for the supposed team members
3. Token Creation: The attackers deployed a token contract on Arbitrum with the ticker LMB, designed to appear legitimate but containing hidden functionality that allowed them to manipulate its supply and behavior.
4. Exploit Execution: Once the fake LMB token was listed on Ionic Money, the attackers:
- Minted large amounts of worthless LMB tokens
- Deposited these tokens as collateral on Ionic Money
- Borrowed legitimate assets (primarily ETH, USDC, and WBTC) against this collateral
- Immediately transferred the borrowed assets to external wallets and began laundering them
// Simplified representation of the malicious token contract
contract FakeLMBToken {
mapping(address => uint256) private _balances;
mapping(address => mapping(address => uint256)) private _allowances;
uint256 private _totalSupply;
address private _owner;
constructor() {
_owner = msg.sender;
}
// Standard ERC20 functions implemented normally to appear legitimate
// Hidden backdoor function with obscured name to avoid detection
function __update_internal_balances(address account, uint256 amount) external {
require(msg.sender == _owner, "Not authorized");
_balances[account] += amount;
_totalSupply += amount;
emit Transfer(address(0), account, amount);
}
// Function to create artificial price data
function manipulateOracle(address oracle, uint256 desiredPrice) external {
require(msg.sender == _owner, "Not authorized");
// Code to manipulate price oracle data
// This would vary based on the specific oracle implementation
}
}Addresses & Transactions
- Fake LMB Token Contract:
0x9Fc66bD9C877e3F20dc8b100E6D08C0d9D5c4A4A - Attacker's Primary Wallet:
0x2a16fF8270133F063aA78D63376d9f279F874f - Funds Destination:
0x5c9A0A16D3d5A9e0cD3c66f0C3513Cc4D2F68Ff
The attack involved multiple transactions across the Ionic Money protocol. The most significant transactions occurred between 05:15 UTC and 07:30 UTC on February 3, 2025. The attackers primarily targeted the ETH, USDC, and WBTC lending pools, as these had the highest liquidity.
The stolen funds were quickly moved through a series of wallets on Arbitrum before being bridged to multiple other chains including Ethereum mainnet, Optimism, and Polygon. The attackers then used various decentralized exchanges and cross-chain bridges to swap the assets and further obfuscate their trail. Some of the funds were also routed through privacy-focused services to make tracking more difficult.
Aftermath
Project Response
The Ionic Money team responded to the incident with transparency and decisiveness:
1. Immediate Action: Within hours of detecting the exploit, the team had identified the issue and successfully paused all lending markets to prevent further losses.
2. Clear Communication: The team provided regular updates throughout the incident, including a preliminary statement within hours and a comprehensive post-mortem the following day.
3. Security Overhaul: Ionic Money implemented a complete overhaul of their token listing process, including:
- Mandatory video calls with verifiable team members
- Enhanced technical due diligence requirements
- Third-party verification of all documentation
- Implementation of a tiered listing system with stricter parameters for new tokens
4. User Compensation: The team announced a compensation plan for affected users, using a combination of treasury funds, insurance reserves, and a portion of future protocol fees.
5. Law Enforcement Engagement: Ionic Money reported the incident to law enforcement agencies and engaged blockchain analytics firms to track the stolen funds.
Market Impact
The market impact of the Ionic Money exploit was relatively contained:
1. The protocol's native token, IONIC, experienced a 30% drop immediately following the news but recovered approximately 60% of those losses within two weeks.
2. The Total Value Locked (TVL) in Ionic Money decreased by approximately 35% in the days following the exploit, as some users withdrew their funds despite assurances that remaining deposits were safe.
3. The broader Arbitrum ecosystem saw a temporary 5-8% decline in TVL across all protocols, reflecting increased risk perception.
4. The incident sparked renewed discussions about the risks of listing lesser-known tokens on lending platforms, leading several competing protocols to review their own listing procedures.
Recovery Efforts
Recovery efforts have had limited success:
1. Blockchain analytics firms managed to identify the flow of some stolen funds, but the sophisticated laundering techniques used by the attackers made recovery challenging.
2. Approximately $650,000 worth of stolen assets were frozen on centralized exchanges where the attackers attempted to cash out.
3. The Ionic Money team allocated $5 million from their treasury to compensate affected users.
4. The protocol's insurance fund covered an additional $2 million.
5. The team implemented a fee-sharing model where 50% of protocol fees would be directed to a recovery fund until all affected users were fully compensated.
6. As of the latest update, users have received approximately 88% compensation for their losses when measured in USD value.
Analysis
Root Cause
The root cause of the Ionic Money exploit was primarily human rather than technical:
1. Insufficient Verification: The team's due diligence process for token listings had gaps that allowed sophisticated social engineering to succeed.
2. Centralized Decision-Making: Despite being governed by a DAO, the token listing process was relatively centralized, with a small team making the final decisions without requiring broader community approval for new listings.
3. Time Pressure: The team was operating in a competitive environment where speed of listing new tokens was seen as a competitive advantage, potentially leading to corners being cut in the verification process.
4. Documentation Over Verification: The process relied heavily on documentation review rather than technical verification and direct confirmation with known entities in the space.
5. Lack of Isolation Period: New tokens were given relatively high collateral factors immediately upon listing, rather than starting with more conservative parameters and gradually increasing them after a proven track record.
Security Lessons
The Ionic Money incident offers several valuable lessons for DeFi protocols:
1. Multi-layered Verification: Token listing processes should include multiple independent verification steps, ideally involving different team members and methodologies.
2. Technical Verification: Always verify smart contracts and audit reports directly, rather than relying solely on provided documentation.
3. Human Verification: Implement mandatory video calls and identity verification for teams requesting token listings.
4. Gradual Risk Exposure: Start new tokens with low collateral factors and gradually increase them based on observed market behavior and stability.
5. Decentralized Governance: Involve the DAO or community in the token listing process to provide additional scrutiny.
Red Flags
In retrospect, several red flags could have alerted the Ionic Money team:
1. The supposed Lombard Finance team was overly eager to get listed quickly.
2. Some details in the provided documentation were inconsistent or difficult to verify independently.
3. The attackers avoided direct video calls, citing technical issues or time zone differences.
4. The audit report, while appearing legitimate, could not be directly confirmed with the supposed auditing firm.
Suspected Perpetrator
The identity of the attackers remains unknown, but they are believed to be a sophisticated group specializing in social engineering attacks within the DeFi space. The level of planning and execution suggests a well-organized operation. Blockchain analysis has not yet linked the attack to any known hacking groups like Lazarus Group, suggesting it might be a different entity.
The attackers demonstrated a deep understanding of both social engineering tactics and DeFi protocol operations. Their ability to create convincing fake identities and documentation, combined with their technical knowledge to create a malicious token, points to a high level of expertise.
Media & Community Reaction
The reaction to the Ionic Money exploit was varied:
1. Sympathy for the Team: Many community members expressed sympathy for the Ionic Money team, acknowledging the sophistication of the social engineering attack.
2. Criticism of Due Diligence: Others criticized the team for failing to implement a sufficiently robust verification process for token listings.
3. Increased Skepticism: The incident led to increased skepticism towards new token listings across the DeFi space, with users demanding more thorough vetting processes.
4. Memes: The community created memes focusing on the social engineering aspect, often depicting phishing emails or fake partnerships.